“Companies must have a view on what ‘state of the art’ means to them – and be prepared to defend that view.” Palo Alto Networks, May 2017
Cybersecurity has evolved from perimeter defence to a more nuanced approach, identifying and protecting the most important nodes, services and applications at the scale of an organisation or network of companies. State of the Art reports (SOAR) on technical and tactical controls were released by the US Defense Information Technology Center in 2000, 2007 and 2009((LaPadula, L.L. (1999; updated September 2000), ‘State of the Art in CyberSecurity Monitoring’, MITRE MP 99B0000020R1; Software Security Assurance, State-of-the-Art Report (SOAR), 31 July 2007 [http://www.dtic.mil/dtic/tr/fulltext/u2/a472363.pdf]; Measuring Cyber Security and Information Assurance, State- of-the-Art Report (SOAR), 8 May 2009 [https://www.csiac.org/wp-content/uploads/2016/02/cybersecurity.pdf])). Similarly, in 2014 the EU Network and Information Security Platform Working Group 3 (WG3), composed of industry and academic expertise, evaluated the tools and techniques required for a secure IT landscape, with particular focus on IoT and cloud((NIS Platform Working Group 3, Secure ICT Landscape, July 2014.)). There is no current single, global definition of State of the Art (SOA) cybersecurity, but descriptions of priority technologies and cutting-edge research are indicative of the scope of today’s solutions.
Cloud workload protection platforms enable a single security policy irrespective of where the workload is running
Cloud Access Security Brokers (CASB) provide a single point of control over multiple cloud services
Isolated, remote browser sessions reduce the chances of malware being introduce to the user’s operating system
Deception technologies confuse and disrupt automated attacks, delay a breach and can now span multiple layers within the enterprise
Endpoint Detection and Response (EDR) solutions monitor unusual behaviour throughout the network; by 2020, 80% of large enterprises will use EDR
Managed Detection and Response (MDR) is popular among small and midsize organisations who want outsourced real-time threat detection
Microsegmentation limits damage from a breach, like bulkheads in a submarine
Software Defined Perimeters create secure, virtual enclaves with restricted access that are protected from public discovery
Software Composition Analysis (SCA) and OSS Security Scanning continuously analyses source code, modules, frameworks and libraries to detect security vulnerabilities before they get into enterprise software
Secure containers combat the problem of using a shared operating system model
Anonymisation of user data, particularly patient data, protects individuals’ privacy; differential privacy introduces random noise to a dataset to protect information when datasets are aggregated
Encryption is increasingly used to secure communications, but raises challenges for law enforcement agencies
Priority cybersecurity technology and research domains, 2017 (source: Gartner; Royal Society; BSI)
Contemporary cybersecurity has evolved from an era of prevention to an ecosystem of dynamic adaptation. Tools that enable cyber attack are also part of today’s cyber defence. Among them, Artificial Intelligence (AI) is likely to become both a weapon and a means of protection in cyberspace. At present, the state of security-by-design in AI is similar to the state of cybersecurity in the mid 1990s – i.e. vulnerable – and the current lack of security in the IoT; for this reason, “business leaders are advised to familiarize themselves with the cutting edge of AI safety and security research”((Yampolskiy, R.V. (2017), ‘AI Is the Future of Cybersecurity, for Better and for Worse’, Harvard Business Review, 8 May 2017 [https://hbr.org/2017/05/ai-is-the-future-of-cybersecurity-for-better-and-for-worse])). 2018 is likely to be the year that banks assume a central role in identity verification and AI is utilised at scale((EIU (2017), ‘Industries in 2018: A special report from the Economist Intelligence Unit’ [http://www.eiu.com/industry])).
While SOA technology assessments are lacking, countries and industries are seeking better cybersecurity through regulation and standards.
The US NIST Cybersecurity Framework, initially released February 2014, is designed to help organisations understand their cybersecurity risk management priorities and design an effective response((US NIST Cybersecurity Framework [https://www.nist.gov/cyberframework/draft-version-11])). In June 2016, the US NIST released a cybersecurity self-assessment tool((US NIST self-assessment tool [https://www.nist.gov/baldrige/products-services/baldrige-cybersecurity- initiative#bceb])), aimed at US businesses but more widely applicable.
The European Cyber Security Organisation provides a complete overview of cybersecurity standards and certification schemes, first released in June 2017 and updated in December 2017((European Cyber Security Organisation, State of the Art Syllabus, Overview of existing Cybersecurity standards and certification schemes (v2), December 2017 [http://www.ecs-org.eu/documents/uploads/updated-sota.pdf])). These include generic standards, professional certifications as well asstandards designed for specific components (e.g. cloud, payment systems) and industries (e.g. energy, telecommunications).
The cybersecurity knowledge ecosystem is evolving around the security professionals who are the front line of defence; the best place to learn about SOA is therefore from the people and companies who live cyber, daily. The language, tools and tactics of SOA cybersecurity are found in the conferences, industry op-eds((see e.g. ‘Best security software: How 5 cutting-edge tools tackle today’s threats’, CIO Online, 28 February 2018 [https://www.csoonline.com/article/3206685/security/best-security-software-how-5-cutting-edge-tools-tackle- todays-threats.html])) and consultancies that represent today’s €100 billion cybersecurity industry.
The EU GDPR and the NIS Directive((The European Commission Digital Single Market, Directive on security of network and information systems [https://ec.europa.eu/digital-single-market/en/network-and-information-security-nis-directive])) require companies to implement ‘state of the art’ cyber defence but are vague on its definition, in part because the threat landscape and solutions are developing more rapidly than legislation((‘European Union Cybersecurity-Related Legislation: Resolving the “State of the Art” Paradox’, Palo Alto Networks Executive Advisory Report, May 2017 [https://www.securityroundtable.org/wp- content/uploads/2017/05/eu-cybersecurity-legislation-executive-advisory-report.pdf])); companies should infer that the choice and implementation of SOA is the responsibility of their CISO. At the core of the EU directives, guidelines for Boards and the global cybersecurity dialogue is the recognition that, beyond technology, human collaboration and communication are vital to effective cybersecurity.
The human factor – Rise of the CxO
Companies have recognised the security risks around holding and using data since the advent of digitised information management as a discrete business discipline, circa 1991. Chief Information Officers (CIOs) have occupied visible roles, particularly in US defence and government contractors, since the mid 1990s. In August 1995, Citibank discovered their security had been breached and more than €8 million stolen((‘Hacking Theft of $10 Million From Citibank Revealed’, Los Angeles Times, 19 August 1995 [http://articles.latimes.com/1995-08-19/business/fi-36656_1_citibank-system\)). CEO John Reed composed an executive search team, who created the role of what is widely regarded as the world’s first Chief Information Security Officer (CISO). After months of searching, Citigroup appointed Steve Katz((‘Unsung (And Under-Sung) Heroes Of Security’, Dark Reading, 25 May 2016 [https://www.darkreading.com/vulnerabilities—threats/unsung-(and-under-sung)-heroes-of-security/d/d- id/1325625])). Then as now, Katz views information security not as a technology issue, but as a business challenge((‘The world’s first CISO explains why technology alone has never beaten cyber crime’, Information Age, 7 January 2015 [http://www.information-age.com/worlds-first-ciso-explains-why-technology-alone-has-never- beaten-cyber-crime-123458809/])).
Where organisations lack the situational awareness to learn during an incident, the strategic response will be reactive((Onibere, M., Ahmad, A. and Maynard, S. (2017), ‘The Chief Information Security Officer and the Five Dimensions of a Strategist’, PACIS 2017 Proceedings, #77 [http://aisel.aisnet.org/pacis2017/77])). A 2016 survey of US firms who had experienced a breach during the period 2009- 2015 found that the organisational response was indeed largely reactive, with firms hiring a CISO for the first time after a major beach, often requiring a complete reorganisation of their enterprise IT strategy((Karanja, E. (2017), ‘The role of the chief information security officer in the management of IT security’, Information and Computer Security, 25: 3, pp.300-329, doi: 10.1108/ICS-02-2016-0013)).
Hired CISOs within the same timeframe generally came from outside the organisation((Karanja, E. and Rosso, M. A. (2017), ‘The Chief Information Security Officer: An Exploratory Study,’ Journal of International Technology and Information Management, 26:2, Art. 2. [http://scholarworks.lib.csusb.edu/jitim/vol26/iss2/2])), affecting knowledge management practice around cybersecurity in two ways: (i) increased chances of standardisation of best-practice among companies across disparate industries; (ii) challenges for internal reconfiguration of practices and protocols, as new knowledge is introduced and new standards mandated. Proactive cybersecurity today includes not only the tools and methods to monitor and mitigate a security breach, but also the ‘soft skills’ to facilitate communication about risk and response, across the C-suite and beyond.
The CERT Division at SEI, Carnegie Mellon University, have dedicated almost two decades to the study of how organisations respond to cybersecurity threats. They identify four functions of today’s CISO((Allen, J. and Mehravari, N. (2015), ‘Structuring the Chief Information Security Officer Organization’, CERT Division, SEI, Carnegie Mellon University [https://resources.sei.cmu.edu/asset_files/Webinar/2016_018_100_453895.pdf])), whose primary role is to:
- protect, shield and defend the organisation and prevent breaches;
- monitor, detect and hunt new and emerging threats;
- enable the organisation to respond and recover from an attack and sustain cyber defence;
- oversee the organisation’s information security management, governance and compliance, education and risk management.
These functions have evolved over time in response to a threat landscape that is (i) pervasive, (ii) rapidly evolving and (iii) causes harm far beyond the IT infrastructure, by disrupting business operations and damaging brand value.
While no two industries are exactly alike, the role of today’s typical CISO((Onibere, M., Ahmad, A. and Maynard, S. (2017), ‘The Chief Information Security Officer and the Five Dimensions of a Strategist’, PACIS 2017 Proceedings, #77 [http://aisel.aisnet.org/pacis2017/77])) can broadly be defined as an information security professional, who also has:
- detailed understanding of the organisation and specific industry context;
- total focus on business objectives, aligning security strategy with core business;
- creative risk management abilities, continually optimising available security resources (human and digital);
- excellent skills in conflict resolution, communication, collaboration;
- influence over the right decision-leader at the right moment, to achieve support for sustained security investment and rapid response when required.
In addition to deep knowledge about information technology and its scope for application across the business, the CISO must know how IT security blocks or enables business risk management, preferably gained through practical experience of working in other roles((Harkins, M.W. (2016) The 21st Century CISO. In: Managing Risk and Information Security. Springer / Apress, Berkeley, CA. doi: 10.1007/978-1-4842-1455-8_10)). Beyond delivering information security assurance across the business, today’s CISO is also required to serve as a business strategist. This task has five dimensions((Onibere, M et al. (2017), op. cit.)):
- innovation and lateral thinking;
- contextual awareness of the issues and threats shaping the industry;
- rapid translation of abstract vision into practical action;
- adaptation of human and digital systems to new threats and opportunities as they occur;
- advocacy and influence.
These broad responsibilities place a burden of trust on the CISO which is a test both of personal integrity and the ability to inspire trust among others((Harkins, M.W. (2016), op. cit.)). Much like a military officer in command of tools and tactics against an invisible and rapidly evolving enemy that respects no boundaries, today’s CISO must be resilient, loyal, adaptive and creative.
Insider threat … insider advantage?
The ‘big issue’ of 2016, insider threat refers to security breaches that occur through deliberate act by company workers and contractors (e.g. misuse of access privileges, theft and sale of corporate data) and/or negligence((Colwill, C. (2009), ‘Human factors in information security: The insider threat – who can you trust these days?’, Information Security, 14.4, pp.186-196.)) (employees who, through lack of awareness or knowledge about data sensitivity and security protocol, expose their organisation to cyber attack((BAE Systems (2016), ‘The Unusual Suspects’ [https://www.baesystems.com/en/cybersecurity/feature/the- unusual-suspects]))) (see figure 2).
The insider threat is not a new phenomenon: it is well characterised in the US military and the nuclear energy sector((Bunn, M. and Sagan, S.D. (2017). Insider Threats. Ithaca: Cornell University Press.)) and was first discussed in the context of information security almost 20 years ago((Anderson, Robert H., et al. (2000), ‘Research on Mitigating the Insider Threat to Information Systems’. Proceedings of a Workshop held August 2000, Arlington, VA. Santa Monica: RAND Corporation.)). In the digital age, the problem has new significance at a larger scale and across a broader attack surface, than ever before.
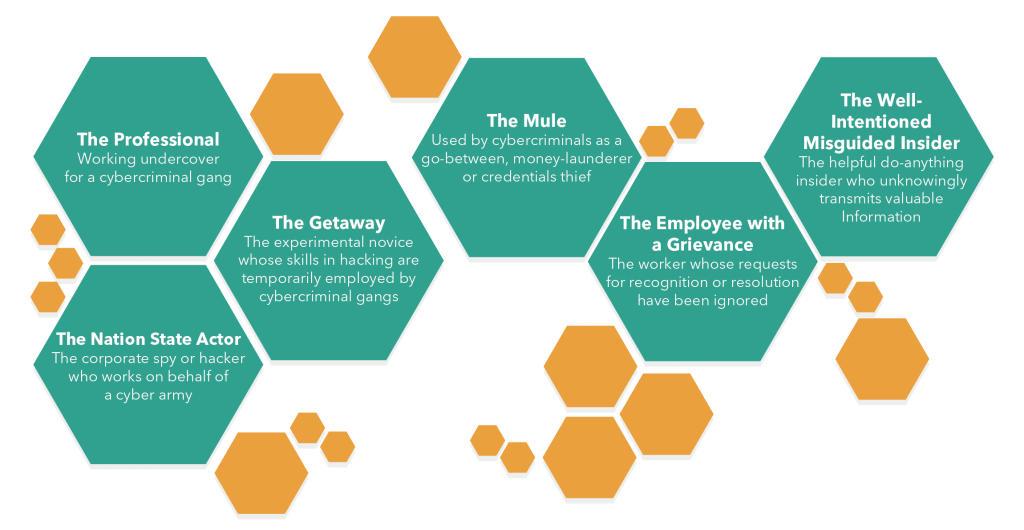
Figure 2: A typology of insider threats (adapted from BAE Systems (2016)((BAE Systems (2016, op. cit.)))
The challenges in protecting corporate data from deliberate or unintended abuse and disclosure are compounded by three factors:
- Securing business operations in the era of remote working and the Bring Your Own Device (BYOD) workplace;
- Maintaining security across remote teams and third-party suppliers who are using many different devices, platforms and security protocols;
- The costs and information management burden of identifying and motivating a disengaged workforce((Gallup, ‘State of the Global Workforce’, 2017 [http://news.gallup.com/reports/220313/state-global-workplace- 2017.aspx])).
Beyond using AI and network monitoring to profile and identify potential insider threats((Moore, Andrew P., Kirk A. Kennedy and Thomas J. Dover. “Introduction to the special issue on insider threat modeling and simulation.” Computational and Mathematical Organization Theory, 22 (2016): 261-272.)), companies have during the past few years begun to recognise the value of Organisational Network Analysis (ONA) to better understand their vulnerabilities to deliberate or unintentional internal security breach. The same techniques used to identify insider threats can also be employed in building a stronger cyber defence, identifying and empowering individuals who are skilled in ‘thinking like the adversary’.
Companies can utilise ONA to audit workforce capabilities for in-house skills and capabilities that may be readily adapted to the cybersecurity challenge((Daultrey, S. (2017), ‘Insider advantage’, 4 December 2017 for viaresource.com [https://www.viaresource.com/blog/blog/insider-advantage])). Short-term ‘wins’ include hiring ‘hacker strategists’, stress-testing digital and knowledge networks, controlling access privileges from within – all of which may be more effective in terms of resources, time and cost, than defending the perimeter, outsourcing protection or surmounting the privacy rights issues with behaviour profiling. Long-serving employees carry with them a corporate memory that can be drawn upon in times of crisis: the time and effort dedicated to building and protecting the corporate knowledge-base is itself a vital part of successful cybersecurity strategy.
Cyber needs everyone
The ‘cyber skills deficit’ has been widely discussed since 2015((‘Cyber security sector struggles to fill skills gap‘, Financial Times, 18 November 2015. The issue was widely discussed throughout 2016, see e.g. RSA2016; 2016 UK Cybersecurity Summit.)) and was a regular headline feature at conferences and expos((‘The Cybersecurity Skills Shortage’, Cipher Brief, 21 February 2016 [https://thecipherbrief.com/article/techcyber/cybersecurity-skills-shortage])) throughout 2015 – 2017. The 2015 ISC(2) global workforce survey identified a shortfall of 1.5 million skilled cyber professionals by 2020. In the past decade, organisations have increasingly outsourced their cybersecurity((CISCO (2015), op. cit.)) to third-party providers and consultants, with certified professionals in a demand-driven market commanding very high fees((‘Cyber Security: the cost of immaturity’, The Economist, 12 November 2015)). In the US, the financial services sector saw an increase of 137% over the five years to 2015 for cybersecurity professionals, with hybrid finance-cyber jobs among the most difficult hiring challenges((Burning Glass (2015), ‘Job Market Intelligence: Cybersecurity Jobs, 2015’ [http://burning-glass.com/wp- content/uploads/Cybersecurity_Jobs_Report_2015.pdf])), ((Financial Times (2015), ‘Cyber security sector struggles to fill skills gap’)).
Throughout 2018, demand in the US for cybersecurity professionals is likely to continue to outstrip supply, particularly in healthcare and financial services((‘7 IT salary and hiring trends for 2018’, CIO, 2 November 2017 [https://www.cio.com/article/3235905/hiring- and-staffing/it-salary-and-hiring-trends-for-2018.html])). The continued talent shortage is likely to affect global perceptions about the state of the global cybersecurity workforce, driving up hiring costs. With the launch of the EU GDPR (effective May 2018), Data Protection Officers (DPO) are likely to be in high demand: an additional 28,000 will be required in Europe alone((‘Rise of the data protection officer, the hottest tech ticket in town’, Reuters, 14 February 2018 [https://www.reuters.com/article/us-cyber-gdpr-dpo/rise-of-the-data-protection-officer-the-hottest-tech-ticket-in- town-idUSKCN1FY1MY])).
A closer look at the current cyber ‘skills shortage’ indicates that:
- It is mostly a US and UK problem;
- The perceived deficit is partly due to the difference between what companies are willing to pay, and what technical proficiencies actually cost (in terms of time and financial resources((Fulton, E., Lawrence, C., Clouse, S. (2013), White Hats Chasing Black Hats: Careers in IT and the skills required to get there, Journal of Information Systems Education, 24(1), 75-80)));
- Training / finding more graduates in computer science and programming is not the solution because: (i) the requirement is immediate; and (ii) cybersecurity is a business risk management problem, requiring a broader skillset and repurposing of existing knowledge assets((CISCO (2015), ‘Mitigating the cybersecurity skills shortage’)).
Cybersecurity is an organisational change problem
The scale, pace and reach of today’s cyber threats requires a whole-of-the-organisation response((Onibere, M. et al. (2017), op. cit.)), demanding unprecedented organisational change both within companies and across the digital and physical supply chains. Companies are actively analysing the skills they have in-house than can be adapted. Thinking laterally – about roles other than IT – opens scope for hiring people from non-IT background that can make a valuable contribution to managing cyber risk((van Zadelhoff (2017), ‘Cybersecurity Has a Serious Talent Shortage. Here’s How to Fix It’, Harvard Business Review [https://hbr.org/2017/05/cybersecurity-has-a-serious-talent-shortage-heres-how-to-fix-it)). Managing the introduction of new technology and knowledge exchange in large organisations needs a combination of leadership, patience, devolved trust – and honest recognition that not everyone cares as much as they should, or could.
Most organisations today realise that the quality of their cybersecurity extends well beyond perimeter defence. As the internet enables increasingly complex global supply chains to serve broader geographies, so too the cyber threat landscape extends into the disparate third-party service providers and digital service platforms.
Achieving organisational change at this scale across discrete businesses and entire ecosystems, calls for a deliberate and artificial adaptation, rather than natural evolution((Anderson, K. (2017), ‘You say you want an evolution (of your risk management programme)’, Journal of Business Continuity & Emergency Planning, 10:2, pp. 118-123(6) [http://www.ingentaconnect.com/content/hsp/jbcep/2017/00000010/00000002/art00003])): the language, tactics and metrics of cybersecurity must be grafted into existing business practice, rather than adopted through learning. Cyberspace threats have evolved over thirty years: companies that want to survive have less than a tenth this timeframe.
Standards, best-practice and international collaboration
2017 was the year of regulations taking form that have wide-ranging consequences not only for cybersecurity, but for broader risk management and data privacy challenges. Some have emerged out of privacy law, others from the world of critical infrastructure protection and financial services standards.
The more difficult challenge is verifying compliance and adjusting cybersecurity strategy as new problems emerge, across jurisdictional and conceptual boundaries. Cybercrime is an international phenomenon. Criminals use methods that exploit international differences in the capacity and authority of companies, law enforcement agencies and governments to effectively respond((United Nations (2004), ‘A more secure world: our shared responsibility’ [http://www.un.org/secureworld/report2.pdf])). The ‘grey zones’((Schmitt, M.N. (2017), ‘Grey zones in the International Law of Cyberspace’, Yale Journal of International Law [http://www.yjil.yale.edu/grey-zones-in-the-international-law-of-cyberspace/])) in international laws indirectly permit acts that may be considered criminal —if there were enforceable laws to prosecute them as such. The current situation favours the cyber criminal, while the delay between a company noticing a breach, identifying the threat source, locating the correct jurisdictional authority and bringing cybercriminals to justice may be many months or years after the crime is committed.
While there is (currently) no international law governing cyberspace, since 2009 nation states have signed 33 multilateral and 30 bilateral agreements on global action to counter cybercrime((Carnegie Endowment for International Peace, op. cit.)).
Provisions of other international conventions also apply in cyberspace, for example the UN Convention against Transnational Organized Crime((United Nations Convention against Transnational Organized Crime [https://treaties.un.org/Pages/ViewDetails.aspx?src=IND&mtdsg_no=XVIII-12&chapter=18&lang=en#top])); and countries collaborate to identify and prosecute cyber criminals using the frameworks provided through INTERPOL, the Budapest Convention, the Wassenaar Agreement and extradition treaties((Daultrey, S. (2017), ‘Cybercrime: invisible problems, imperfect solutions’ [https://sdaultrey.net/downloads/Daultrey-S-Cybercrime-07-2017.pdf])). The Tallinn Manual, first produced in 2013 and updated in 2017, is the only document currently in existence that sets out an agreed basis on which states may assess the legality of their operations in cyberspace((Schmitt, M.N. (ed.) (2017), Tallinn Manual on the International Law Applicable to Cyber Operations. Cambridge : England. [DOI: 10.1017/9781316822524])) (and infer the margins of responsibility): there is no such equivalent for companies.
While the Tallinn Manual does not consider lawful actions by corporations operating in cyberspace, its logic does provide a framework on which the responsibilities of companies may be systematically evaluated (see figure 3).

Figure 3: A structured approach to cybersecurity at the scale of a company. Questions are examples of the responsibility ‘audit’ that should be performed before cybersecurity strategy is drafted, identifying the people, processes, systems, data and compliance standards that are implicated across the organisation.
Tallinn considers jurisdictional limits (ch. 1), existing laws and protocols that apply in responding to cybercrime, proportionality of response (ch. 5) and the rights of individuals. Similarly, companies’ existing policy on, say, intellectual property theft, finds ready applicability in cyberspace; and as corporate citizens, companies can call upon the existing laws and protocols of their host countries (e.g. anti-fraud, counter-terrorism) to seek prosecution for cybercrimes that affect people and services beyond the corporate perimeter.





